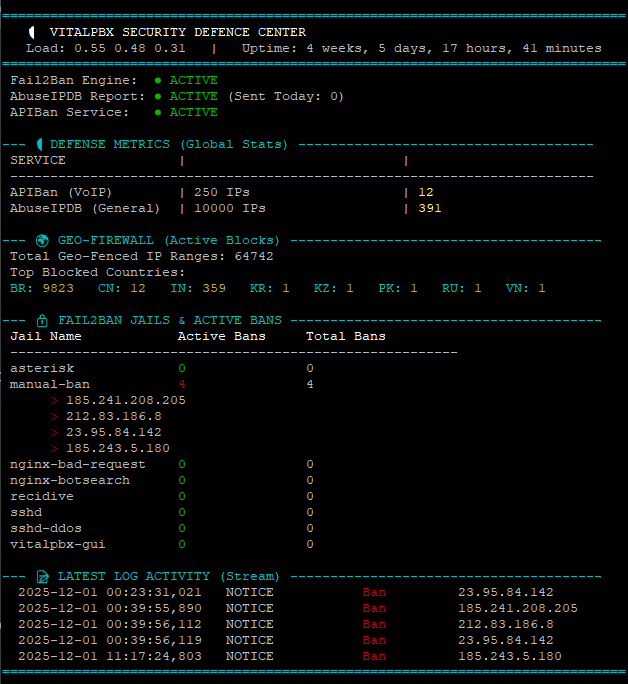
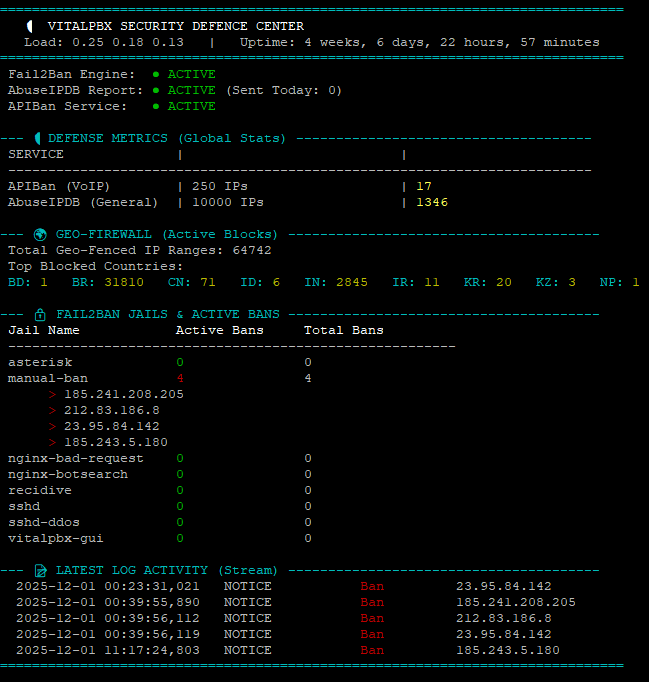
Here is Gemini’s take on the situation..
Here is the complete, step-by-step guide to setting up a “Real-Time” IDS-like blocklist on Debian using ipset and iptables.
This method is superior to Fail2Ban for this specific task because it blocks traffic at the kernel level (extremely fast) before it even hits your application logs.
Prerequisites
You need a free API key from AbuseIPDB.
- Log in to AbuseIPDB.
- Go to API (in the menu) → Create Key.
- Copy this key; you will need it for the script below.
Step 1: Install Required Tools
We need ipset to manage the list of IP addresses and curl to download the list. We will also install iptables-persistent to save our firewall rules.
Run the following commands as root (or use sudo):
Bashsudo apt update sudo apt install ipset ipset-persistent iptables-persistent curl -y
(During installation, if asked to save current IPv4/IPv6 rules, select Yes).
Step 2: Create the Blocklist Script
We will create a robust script that:
- Downloads the blacklist from AbuseIPDB.
- Creates a temporary list and fills it (to prevent firewall downtime).
- Swaps the temporary list with the live list (Atomic update).
Create the file:
Bashsudo nano /usr/local/bin/abuseipdb-blocklist.sh
Paste the following code into the file. Make sure to replace YOUR_API_KEY_HERE with your actual key.
`Bash#!/bin/bash
— CONFIGURATION —
API_KEY=“YOUR_API_KEY_HERE”
ipset_name=“abuseipdb”
ipset_type=“hash:ip”
limit=10000 # Free account limit is 10,000
confidence=100 # Only block 100% sure bad IPs
---------------------
1. Create the ipset if it doesn’t exist yet
if ! sudo ipset list -n | grep -q “$ipset_name”; then
sudo ipset create “$ipset_name” “$ipset_type”
fi
2. Create a temporary set for atomic swapping
temp_ipset=“${ipset_name}_temp”
sudo ipset create “$temp_ipset” “$ipset_type”
sudo ipset flush “$temp_ipset”
3. Download the blacklist
We prefer plaintext for speed and easy parsing
response=$(curl -s -G https://api.abuseipdb.com/api/v2/blacklist
-d confidenceMinimum=$confidence
-d limit=$limit
-d plaintext
-H “Key: $API_KEY”
-H “Accept: text/plain”)
Check if we actually got a list of IPs (simple validation)
if [[ $response =~ [0-9]+.[0-9]+.[0-9]+.[0-9]+ ]]; then
echo “AbuseIPDB: Downloading and updating blocklist…”
# 4. Add IPs to the temporary set
for ip in $response; do
sudo ipset add "$temp_ipset" "$ip" -exist
done
# 5. Swap the live set with the temp set
sudo ipset swap "$temp_ipset" "$ipset_name"
# 6. Destroy the temp set
sudo ipset destroy "$temp_ipset"
echo "AbuseIPDB: Blocklist updated successfully with $(echo "$response" | wc -l) IPs."
else
echo “AbuseIPDB: Error downloading list or empty response.”
echo “Response: $response”
fi`
Save and exit (Ctrl+O, Enter, Ctrl+X).
Make the script executable:
Bashsudo chmod +x /usr/local/bin/abuseipdb-blocklist.sh
Step 3: Configure the Firewall (Iptables)
Now we need to tell the firewall to look at this ipset and drop anyone on it.
- Run the script once to create the list and populate it:
Bashsudo /usr/local/bin/abuseipdb-blocklist.sh
- Add the Block Rule to
iptables. This rule says "If the source IP is in the ‘abuseipdb’ list, DROP the packet."Bashsudo iptables -I INPUT -m set --match-set abuseipdb src -j DROP(Note: -I INPUT puts this rule at the very top, so it runs before any other rules).
Step 4: Ensure Persistence (Surviving Reboots)
If you reboot now, the rules will disappear. We need to save them.
- Save the IPSet list: Debian’s
ipset-persistent plugin usually handles this, but let’s manually ensure the config is saved.Bashsudo ipset save > /etc/iptables/ipsets
- Save the Iptables rules:
Bashsudo netfilter-persistent save
Verification: To verify this works, you can reboot your server and run sudo iptables -L -n and sudo ipset list to ensure the rules and lists are still there.
Step 5: Automate with Cron
You need this list to update automatically. Since AbuseIPDB updates frequently, running this every 4 to 12 hours is standard.
- Open the root crontab:
Bashsudo crontab -e
- Add this line to the bottom:
Bash# Update AbuseIPDB Blocklist every 4 hours 0 */4 * * * /usr/local/bin/abuseipdb-blocklist.sh > /dev/null 2>&1
How to check if it’s working
To see how many attacks you are blocking, run:
Bashsudo iptables -L INPUT -v -n
Look for the line referencing abuseipdb. The first column (pkts) shows how many packets have been blocked.
Summary of what you just built:
- Script pulls 10,000 known hackers from AbuseIPDB.
- IPSet stores them efficiently in memory.
- Iptables checks that list instantly for every incoming connection.
- Cron keeps the list fresh automatically.