mo10
November 25, 2021, 12:12am
1
Just by clicking the refresh button on a vitalpbx every second you are able to attack everyone with a vitalpbx online (high CPU and load). You don’t even need to be logged in.
This is even possible with the official vitalpbx Demo:
Do you have an idea how to fix this ASAP?
And why is the WebGui consuming so much resources anytime in general? Any optimization possible?
Real Life example. Every 9 seconds since 5 days:
159.89.120.74 - - [25/Nov/2021:01:10:19 +0100] "POST / HTTP/1.1" 200 20735 "-" "python-requests/2.12.4"
159.89.120.74 - - [25/Nov/2021:01:10:28 +0100] "POST / HTTP/1.1" 200 20735 "-" "python-requests/2.12.4"
159.89.120.74 - - [25/Nov/2021:01:10:37 +0100] "POST / HTTP/1.1" 200 20735 "-" "python-requests/2.12.4"
159.89.120.74 - - [25/Nov/2021:01:10:46 +0100] "POST / HTTP/1.1" 200 20735 "-" "python-requests/2.12.4"
159.89.120.74 - - [25/Nov/2021:01:10:55 +0100] "POST / HTTP/1.1" 200 20735 "-" "python-requests/2.12.4"
This helped, but i guess not for long:
fail2ban-client -vvv set apache-auth banip 159.89.120.74
Thanks a lot.
Placing the gui behind Cloudflare should clear this issue if you only allow traffic from your networks and Cloudflare servers.
mo10
November 28, 2021, 7:55pm
3
The problem persist that the gui uses a lot of resources and can be slow on systems with good SSD and good CPU and enough free RAM.
PitzKey
November 28, 2021, 8:01pm
4
Then this subject should really be addressing the performance/resources usage issues.
miguel
November 29, 2021, 11:48pm
5
On VitalPBX 3.1.4, we’ve included some extra security to avoid requests from non-browser applications like " python-requests/2.12.4
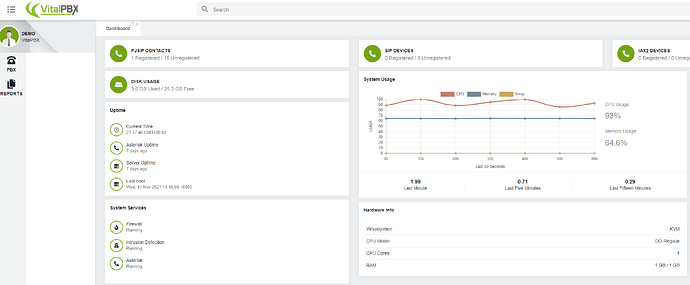
Now, about the Demo server, this server has basic resources. A real PBX server shouldn’t have 1GB of RAM with a single-core CPU.
Actually, retrieving the add-ons list in a server with the same specifications overloads the system.
The screenshot above shows the CPU behavior while downloading the list of available add-ons.
mo10
November 30, 2021, 5:54pm
6
Just updated to latest VitalPBX 3.1.4
Issue is still there:
159.89.120.74 - - [30/Nov/2021:18:51:45 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3079782
159.89.120.74 - - [30/Nov/2021:18:51:55 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3059687
159.89.120.74 - - [30/Nov/2021:18:52:06 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3639702
159.89.120.74 - - [30/Nov/2021:18:52:18 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3083343
159.89.120.74 - - [30/Nov/2021:18:52:28 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3176753
Every 9 seconds. And that IP does not get blocked automatically.
miguel
November 30, 2021, 6:00pm
7
It will get blocked if the server responds with 403. This only works if your server is configured to work over HTTPS only.
mo10
November 30, 2021, 6:06pm
8
Just changed to “Force HTTPS”. Same thing. Not blocking.
159.89.120.74 - - [30/Nov/2021:19:03:45 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3284992
159.89.120.74 - - [30/Nov/2021:19:03:56 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3503710
159.89.120.74 - - [30/Nov/2021:19:04:08 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3070224
159.89.120.74 - - [30/Nov/2021:19:04:19 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3123433
159.89.120.74 - - [30/Nov/2021:19:04:30 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3159024
159.89.120.74 - - [30/Nov/2021:19:04:41 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3493562
159.89.120.74 - - [30/Nov/2021:19:04:52 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3205402
159.89.120.74 - - [30/Nov/2021:19:05:03 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3686720
159.89.120.74 - - [30/Nov/2021:19:05:15 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3236540
159.89.120.74 - - [30/Nov/2021:19:05:26 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3231235
159.89.120.74 - - [30/Nov/2021:19:05:37 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3509861
159.89.120.74 - - [30/Nov/2021:19:05:49 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3457516
miguel
November 30, 2021, 6:17pm
9
Well, share your python script for testing. We did a basic one for testing that kind of attack and fails because the server returns the forbidden HTTP message.
import requests as req
import time
# Take user input
number = 1
# Condition of the while loop
while number < 20:
resp = req.request(method='GET', url="https://demo.vitalpbx.org", verify=False)
print(resp.text)
print("Thank you "+str(number))
# Increment the value of the variable "number by 1"
number = number+1
time.sleep(5)
Response from server
Attacker IP - - [30/Nov/2021:18:13:45 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
Attacker IP - - [30/Nov/2021:18:13:50 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
Attacker IP - - [30/Nov/2021:18:13:56 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
Attacker IP - - [30/Nov/2021:18:14:01 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
Attacker IP - - [30/Nov/2021:18:14:06 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
Attacker IP - - [30/Nov/2021:18:14:11 +0000] "GET / HTTP/1.1" 403 - "-" "python-requests/2.26.0"
These attacks get banned after 50 tries. The server shouldn’t get overloaded because doesn’t charge the website, instead just return a forbidden message.
PitzKey
November 30, 2021, 6:26pm
10
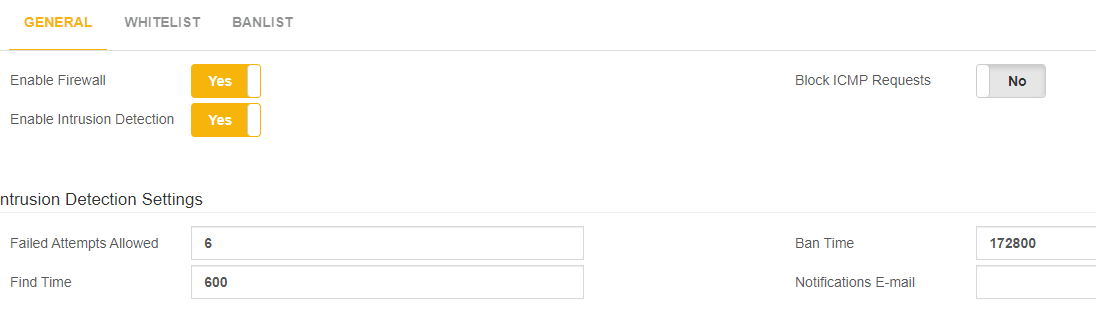
@mo10 How many failed attempts do you allow in your PBX and what is the find time?
mo10
November 30, 2021, 7:51pm
11
@PitzKey
@miguel
I can not share a script since this is a REAL LIFE scenario. It’s an actual attack:https://www.abuseipdb.com/check/159.89.120.74
159.89.120.74 - - [30/Nov/2021:20:48:40 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3436175
159.89.120.74 - - [30/Nov/2021:20:48:51 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3549767
159.89.120.74 - - [30/Nov/2021:20:49:02 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3696442
It is not GET it is POST . And it is Code 200 and not 403.
It is still not okay how much resources one little request can consume. It would be important to optimize consuming resources if not logged in for example. Or better: optimizing the requests in general.
Imagine 5-10 Bots would just request every 9 seconds. It is not okay and not normal to consume so much resources.
Thanks
miguel
November 30, 2021, 7:53pm
12
Ok. Thanks for your input!
1 Like
mo10
November 30, 2021, 8:08pm
13
Please also do a
[ban-forever]
enabled = true
bantime = -1
in
for example so we can ban some ips forever:
fail2ban-client -vvv set ban-forever banip 159.89.120.74
Thx
mo10
November 30, 2021, 10:17pm
15
i know but i don’t want it “permanent” for every IP.
mo10
December 3, 2021, 1:41pm
16
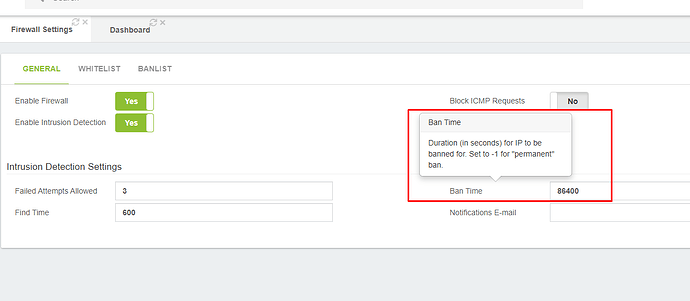
Now my 2 Days Ban-Time are over and here it is again:
159.89.120.74 - - [03/Dec/2021:14:37:02 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3900079
159.89.120.74 - - [03/Dec/2021:14:37:13 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3490747
159.89.120.74 - - [03/Dec/2021:14:37:24 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3754883
159.89.120.74 - - [03/Dec/2021:14:37:35 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 4142571
159.89.120.74 - - [03/Dec/2021:14:37:46 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3501977
159.89.120.74 - - [03/Dec/2021:14:37:56 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3392725
159.89.120.74 - - [03/Dec/2021:14:38:07 +0100] "POST / HTTP/1.1" 200 21483 "-" "python-requests/2.12.4" Time 3541176
We sure need a permanent Ban feature for certain IPs in a special Jail.
And a fix or options for “attacks” like this.
Thanks
miguel
December 4, 2021, 6:39am
17
@mo10
Check on version 3.1.4 R2
1 Like
mo10
December 4, 2021, 8:50am
18
thank you.
159.89.120.74 - - [04/Dec/2021:09:40:00 +0100] "POST / HTTP/1.1" 403 - "-" "python-requests/2.12.4" Time 20774
159.89.120.74 - - [04/Dec/2021:09:40:12 +0100] "POST / HTTP/1.1" 403 - "-" "python-requests/2.12.4" Time 17322
159.89.120.74 - - [04/Dec/2021:09:40:22 +0100] "POST / HTTP/1.1" 403 - "-" "python-requests/2.12.4" Time 11132
159.89.120.74 - - [04/Dec/2021:09:40:33 +0100] "POST / HTTP/1.1" 403 - "-" "python-requests/2.12.4" Time 9328
It tried again but when it did CPU was not going up. Which is good.
This looks good:
[apache-forbidden]
enabled = true
filter = apache-forbidden
logpath = /var/log/httpd/access_log
maxretry = 20
Could you please give us something like this as well for manual BAN forever (not for every IP)?
[ban-forever]
enabled = true
bantime = -1
You will NOT block requests like this. Which is good. You only look for 403.
::1 - - [04/Dec/2021:09:39:56 +0100] "GET /holiday/php/holiday.php?c=USA&t=Default+Timezone HTTP/1.1" 200 10 "-" "VitalPBX"
Again: thanks a lot.